Admin SSO
Authress provides easy access to your account via your existing corporate identity provider. Besides SAML and OpenID, there are a number of first class connections available for AWS, Auth0, Okta, and Microsoft Azure AD (Entra). These options enable your engineering team members to log into Authress without needing to sign up.
Configuring your SSO login
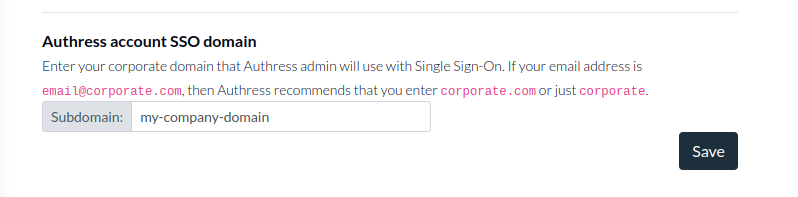
To enable your engineering team to log in with your identity provider, after you specify the configuration for your provider of choice, you'll need to select a custom SSO domain. This domain can be anything you prefer, but must be globally unique. As we will see below, your team will enter this value into the SSO Login screen. The recommendation is to make this the same as your corporate domain without the TLD (.com, .io, .ai). For instance, if your email is user@my-company-domain.com, a good choice would be my-company-domain. For even easier access, you can choose an abbreviation.
Walk-through guides setting up SSO Providers
📄️ AWS
Login to Authress using AWS SSO
📄️ Okta
Login to Authress using your Okta identity
Team member login
Step 1. Selecting SSO Login
Once configured, your team can login using the Continue with SSO option available on the Login screen:
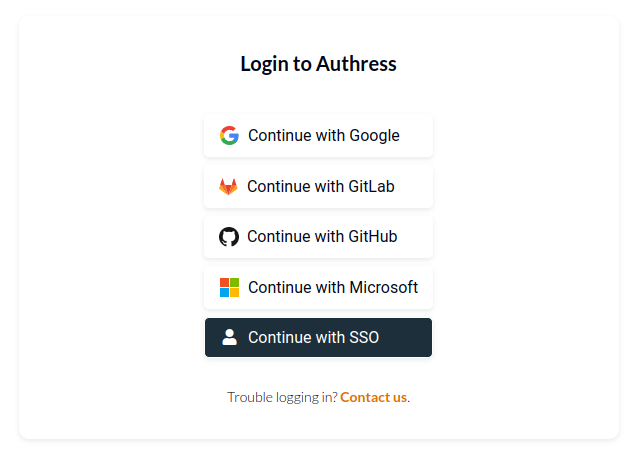
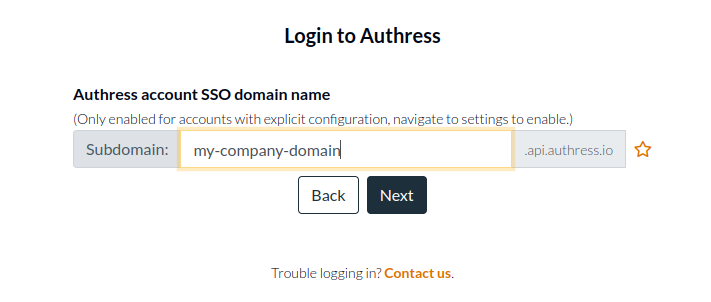
Then they'll enter your domain, to automatically log them in with your configured identity provider. In this example the configuration would have been set to my-company-domain. For more information about how to configure the my-company-domain as your subdomain see configuring your SSO login.
Step 2. Access to the Authress Management Portal
When your team logs in the first time they won't have any permissions to the portal. They will see this message on login:
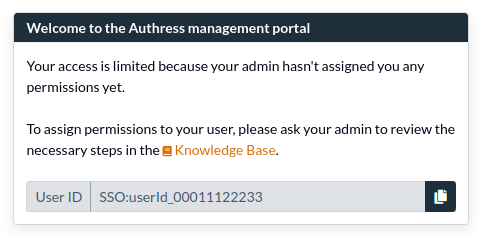
Important: They are seeing this message because although you have configured SSO for them, that only allows them to log in, that doesn't allow them to make changes to your Authress account. The next step is to give them access to the resources in Authress that they need.
That means before your team can use Authress via your SSO, you need to give them permission. This step is the same irrespective of using SSO or not, as all users need explicit access before they are allowed to use the portal. You grant them access the same way you grant anyone access to your Authress resources using access records. The best way grant SSO users admin access is to update your Authress account Root Access Record and add the user's SSO user ID to the list of users. If you want to give them a subset of the full admin permissions you can also create additional access records or user groups.
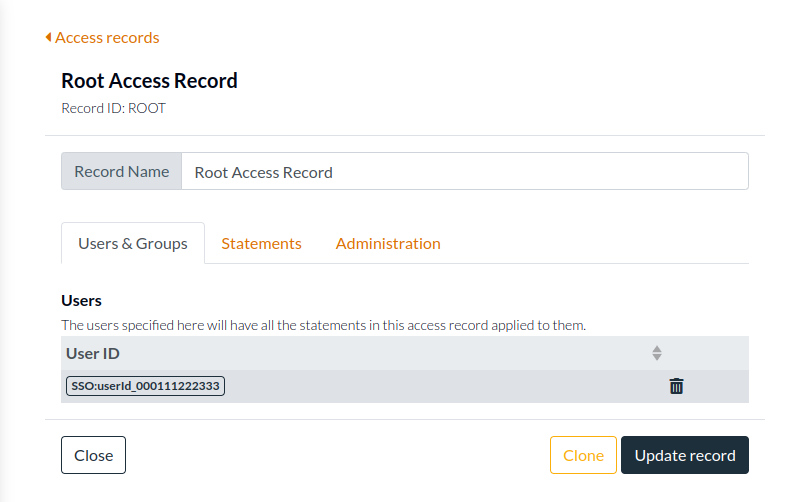
Creating a new record
Instead of editing the Root access record, you can create a new record for the user. What's important to remember is that the permission ✶ (star) is not the same as Authress:✶. ✶ (star) only grants access to your resources, it does not grant access to the Authress Management Portal nor the Authress related resources. Give the user access to the resources: Authress:✶ so they will be to use the portal and update all the Authress related resources--Access Records, Service Clients, Roles.
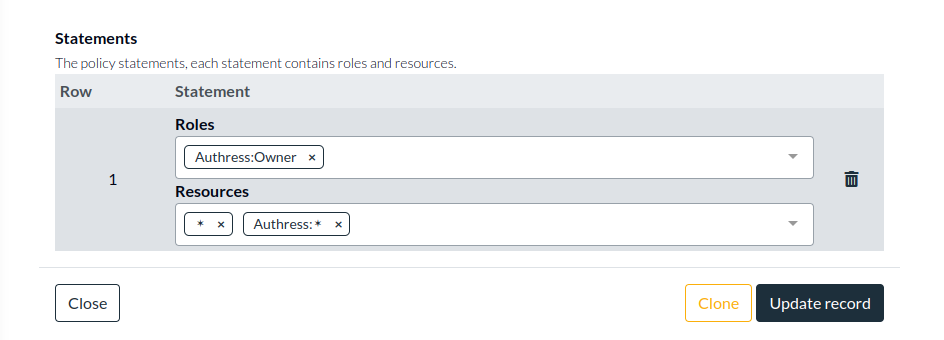
Authress management resources
Alternatively, you can give them specific access to any of the Authress related resources:
Account Management:
Authress:AccountBilling- Change billing for the accountAuthress:AccountBilling/Usage- Review billing metrics (READ) and request updates to usage and rate limits (UPDATE)Authress:Configuration- Configure all aspects of the Authress management account, from integrations to SSO configurationAuthress:Configuration/Integrations- Configure Authress audit trail (integrations:readandintegrations:update)Authress:Configuration/UserAnalytics- Review and manage the user analytics captured and display in Authress, such as the Authress audit trail.
Authorization:
Authress:AccessRecords- Access records that allow them to change permissionsAuthress:AccessRequests- Allow them to create access requests for more permissions and approve others access requestsAuthress:Groups- Create and modify user groups for assigning permissionsAuthress:ResourcePermissions- Update resources public permissionsAuthress:Roles- Create and manage user roles, granting new access and new permissionsAuthress:UserPermissions- Grant access to the Authress Access Analyzer and enable them to check users permissions
Authentication:
Authress:Users- Enabling fetching user data and searching for logged in usersAuthress:Applications- Manage client applicatons for user loginAuthress:Connections- User Authentication configuration and customer SSO loginAuthress:Extensions- Manage platform extensions for external third party developer integration into your platformAuthress:ServiceClients- Generate service clients for interacting with Authress or handling machine-to-machine authenticationAuthress:Tenants- Manage customer tenants and their SSO Configuration
Going further
Authress provides a number of more automated solutions and stronger integrations with certain identity providers. If your team has more complex requirements, please reach out directly to our development team.